Introduction: Why Digital Security Tools Are Essentials
In today’s interconnected world, our lives are increasingly lived online. For many activities, we bank, shop, socialize, learn, and work in the digital realm. While this offers incredible convenience and opportunity, it also exposes us to a growing landscape of sophisticated threats. Indeed, malicious actors are constantly devising new ways to compromise personal data, steal identities, disrupt systems, and invade privacy. Therefore, navigating this digital tightrope requires more than just caution; rather, it demands proactive protection, often achieved through effective digital security tools.
Consequently, relying solely on default settings or hoping for the best is no longer a viable strategy. Building a robust defense using software-based solutions is thus essential for safeguarding your digital activity and online footprint. Therefore, this guide serves as your blueprint, exploring the common threats we face and also introducing the key digital security tools that form the foundation of a secure online experience. Specifically, we’ll delve into what these tools do, why they’re crucial, and then provide recommendations for effective solutions you can often find conveniently on Amazon.
Understanding Threats: The Need for Online Protection Tools
Before diving into the solutions, it’s vital to understand the nature of the threats lurking online. Truly, awareness is the first step towards effective protection. So, here are some of the primary dangers we aim to mitigate with digital security tools:
Malware, Virus, and Ransomware
This broad category encompasses various types of malicious software designed to infiltrate, damage, or disable computer systems and networks. For example, viruses replicate and spread, worms exploit vulnerabilities to propagate, trojans disguise themselves as legitimate software, spyware secretly monitors your activity, and similarly, adware bombards you with unwanted ads. Furthermore, Ransomware is particularly devastating, encrypting your files and subsequently demanding payment for their release. Furthermore, these threats can arrive via email attachments, malicious downloads, infected websites, or even compromised USB drives.
[IMG PLACEHOLDER – CONTEXT: Abstract graphic visually representing different types of malware icons (virus, worm, trojan, ransomware lock) spreading through a network.]
Phishing and Social Engineering
In contrast to exploiting technical vulnerabilities, phishing attacks target human psychology. Typically, scammers send deceptive emails, messages, or create fake websites mimicking legitimate institutions (banks, social media platforms, online retailers) in order to trick you into revealing sensitive information like login credentials, credit card numbers, or personal identifiers. Additionally, social engineering encompasses broader manipulation tactics used to gain trust and extract information or access.
Data Breaches and Identity Theft, & Protective Tools
Large-scale data breaches, where hackers steal vast amounts of user data from company servers, are unfortunately increasingly common. Consequently, This stolen information (usernames, passwords, addresses, financial details) often ends up for sale on the dark web, in turn fueling identity theft. As a result, criminals can use your stolen data to open fraudulent accounts, make unauthorized purchases, or commit other crimes in your name, ultimately potentially ruining your credit and reputation.
Don’t become a victim. Find out if your personal information has been compromised so that you can take action to remove your private data.
Learn More
Online Tracking & Privacy Protection Tools
While not always malicious in intent like malware, pervasive online tracking still raises significant privacy concerns. For instance, advertisers, data brokers, and tech companies collect vast amounts of data about your browsing habits, location, interests, and online behavior, often without explicit consent. Then, This data profile can then be used for targeted advertising, price discrimination, or even sold to third parties. Thus, protecting your digital footprint involves minimizing this unwanted surveillance, often through the use of digital security tools.
Building Your Digital Fortress: Essential Software Security Tools
Understanding the threats underscores the need for a multi-layered defense. No single tool is foolproof; however, combining several key software solutions creates a formidable barrier against most common attacks. Based on our collective experience and industry best practices, these are the core components of a strong digital security setup:
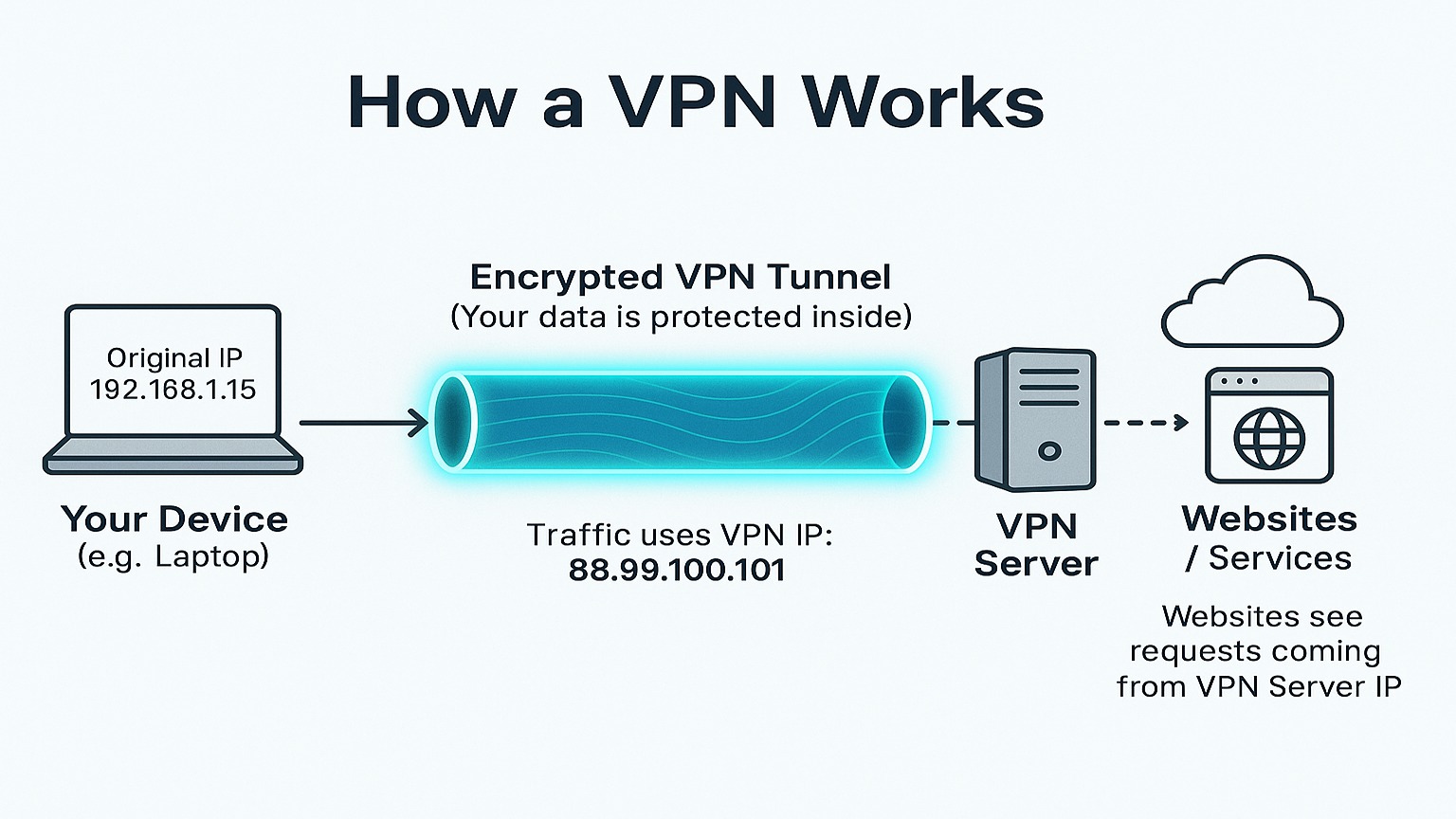
VPN’s: A Key Digital Security Tool for Encryption
Think of your internet connection as a public highway. Without a VPN, obviously, your data travels in the open, potentially visible to your Internet Service Provider (ISP), network administrators (on public Wi-Fi), and eavesdroppers. Conversely, a VPN creates a private, encrypted tunnel for your internet traffic. When you connect to a VPN server, your data is encrypted before it leaves your device, travels securely to the VPN server, and then exits onto the public internet with the VPN server’s IP address, effectively masking your own. As a digital security tool, a VPN is crucial for online privacy.
Why Use a VPN?
- Encryption: Scrambles your data, making it unreadable to anyone intercepting it, which is crucial on public Wi-Fi networks (cafes, airports).
- IP Address Masking: Hides your real IP address, thereby enhancing anonymity and preventing websites and services from easily tracking your location.
- Bypass Geo-Restrictions: Also, it Allows access to content or services that might be blocked in your geographic region (though terms of service should be checked).
- ISP Privacy: Also, it prevents your ISP from logging your browsing activity for potential sale or monitoring.
Top VPN Choices on Amazon
NordVPN: Known for strong security features, a large server network, good speeds, and an audited no-logs policy. Subscription licenses or key cards for NordVPN can often be found for purchase on Amazon, making it an accessible digital security tool. [PRODUCT CTA] [Look for NordVPN Licenses on Amazon]
ExpressVPN: Praised for ease of use, excellent speeds, robust security, and wide device compatibility. While direct subscriptions are primarily purchased through their website, ExpressVPN offers the ExpressVPN Aircove, a secure VPN router, which is available for purchase on Amazon. This hardware solution provides VPN protection for all devices connected to it, serving as a comprehensive digital security tool for your home network.
*Availability of specific subscription codes/cards on Amazon can vary. Always verify the seller and terms.
Antivirus Suites: Malware Protection Tools
Antivirus (AV) and anti-malware software are fundamental digital security tools designed to detect, block, and remove malicious software from your devices (computers, smartphones, tablets). Importantly, modern suites go far beyond simple virus scanning.
- Key Features to Look For:
- Real-Time Protection: First, it Continuously monitors files, applications, and network traffic for threats as they happen.
- Comprehensive Scanning: Moreover, it offers on-demand scans (quick, full system) and scheduled scans to proactively hunt for malware.
- Ransomware Protection: Generally includes specific features to block ransomware behavior and potentially protect important files.
- Web Protection/Anti-Phishing: Often blocks access to known malicious websites and also flags potential phishing attempts.
- Firewall: Typically monitors network traffic, blocking unauthorized access attempts to your device.
- Regular Updates: Finally, it Automatically updates its threat database in order to recognize the latest malware strains.
[IMG PLACEHOLDER – CONTEXT: Screenshot of a generic antivirus software dashboard showing real-time protection status and scan options.]
- Recommended Antivirus/Anti-Malware Suites (Commonly Found on Amazon):
- Norton 360 Deluxe/Premium: A comprehensive suite offering strong malware protection, VPN, password manager, cloud backup, and parental controls depending on the tier. Widely available as physical key cards or digital downloads.
[PRODUCT CTA] [See Norton 360 Plans on Amazon] - McAfee Total Protection: Another popular all-in-one solution providing antivirus, web protection, identity monitoring, VPN, and password manager features. Frequently sold via activation codes/cards.
[PRODUCT CTA] [View McAfee Total Protection on Amazon] - Bitdefender Total Security: Often highly rated for its effective malware detection rates and minimal system impact. Offers multi-layer ransomware protection, VPN, and parental controls. Look for digital codes or subscription cards.
[PRODUCT CTA] [Check Bitdefender Availability on Amazon]
- Norton 360 Deluxe/Premium: A comprehensive suite offering strong malware protection, VPN, password manager, cloud backup, and parental controls depending on the tier. Widely available as physical key cards or digital downloads.
Password Managers: Critical Digital Security Tools for Access
Weak, reused passwords are one of the biggest security vulnerabilities for most individuals. Indeed, remembering dozens of complex, unique passwords for every online account is practically impossible. Therefore, This is where password managers become indispensable digital security tools. Essentially, they securely store all your login credentials in an encrypted vault, protected by a single master password (or biometric).
- Why Use a Password Manager?
- Generate Strong Passwords: Creates long, random, complex passwords that are extremely difficult to crack.
- Secure Storage: Encrypts your password database, thus keeping credentials safe from prying eyes.
- Auto-Fill Convenience: Automatically fills login forms on websites and apps, saving time and also preventing exposure to keyloggers.
- Cross-Platform Sync: Usually access your passwords securely across multiple devices (computer, phone, tablet).
- Security Audits: Additionally, many password managers can flag weak, reused, or potentially compromised passwords stored in your vault.
[IMG PLACEHOLDER – CONTEXT: Illustration showing a password manager vault icon securely storing various login credentials behind a master key lock.]
Leading Password Manager Options
- Recommended Password Managers (Check Amazon for Potential Offers):
- Keeper Security Password Manager: Known for strong security architecture (zero-knowledge), secure sharing options, and business plans. Sometimes offers deals or codes via retailers like Amazon.
[PRODUCT CTA] [Look for Keeper Security Deals on Amazon] - Dashlane Password Manager: Offers a user-friendly interface, robust security features, dark web monitoring, and an integrated VPN (in premium plans). Check for subscription options.
[PRODUCT CTA] [Explore Dashlane Plans (Check Amazon Availability)] - 1Password: Highly regarded for its excellent usability, security focus (Secret Key), and family/team sharing features. Less commonly sold directly on Amazon, but check for any available offers.
[PRODUCT CTA] [See 1Password Options (Check Amazon)] - *Direct software subscriptions are less common on Amazon than activation codes/cards for AV or VPNs. Verify carefully. [LINK SUGGESTION – TYPE: Internal – CONTEXT: Link to a potential site article detailing password security best practices or comparing password managers.]
- Keeper Security Password Manager: Known for strong security architecture (zero-knowledge), secure sharing options, and business plans. Sometimes offers deals or codes via retailers like Amazon.
Additional Digital Security Tools & Practices
Beyond the core trifecta of digital security tools, you should also consider these additional practices for enhanced protection:
Secure Browsers: Browsers like Brave or Firefox with enhanced privacy settings and extensions (like uBlock Origin, Privacy Badger) can significantly reduce tracking and block malicious scripts.
- Multi-Factor Authentication (MFA/2FA): Crucially, enable MFA wherever possible (email, banking, social media). Because This requires a second form of verification (like a code from an app or SMS) in addition to your password, significantly increasing account security.
- Secure Cloud Backup: Regularly back up important files to a secure cloud service or an external drive. This protects against data loss from hardware failure or ransomware attacks.
Integrating Your Digital Security Tools: A Holistic Approach
It’s crucial to understand that these digital security tools work best together. For instance, an antivirus suite protects your device from malware downloads, but a VPN encrypts your connection on insecure networks. Similarly, a password manager secures your accounts, but MFA adds a vital extra layer if credentials are somehow compromised.
For maximum convenience and often cost savings, some users meanwhile prefer comprehensive security suites. Specifically, solutions like Norton 360 and McAfee Total Protection, mentioned earlier, bundle antivirus, VPN, and password management features into a single subscription, thereby offering a streamlined approach to managing your core digital security tools.
Therefore, think of your digital security not as a single product, but instead as an integrated system where each component reinforces the others. Also, regularly update all software (OS, browser, digital security tools) as updates often patch critical vulnerabilities. Finally, stay informed about common scams and always practice safe browsing habits.
Finding Your Digital Security Tools: What to Look For
Amazon offers a convenient platform to purchase activation codes, subscription cards, or sometimes digital downloads for many popular security software brands. So, when shopping:
- Verify the Seller: First, ensure you are buying directly from the software vendor’s official Amazon storefront or a highly reputable authorized reseller. Definitely avoid suspicious third-party sellers.
- Check Compatibility: Next, confirm the software version is compatible with your operating system (Windows, macOS, Android, iOS) and also covers the number of devices you need.
- Understand Subscription Terms: Furthermore, be clear about the subscription length (usually 1 year), renewal policies, and what features are included in the specific tier you are purchasing.
- Read Recent Reviews: Lastly, look at recent customer reviews on Amazon, especially paying attention to comments about the activation process and customer support experience.

Conclusion: Taking Control with Your Digital Security Tools
Protecting your digital life is a continuous journey, not a one-time fix. As threats evolve, so must our defenses. However, implementing core digital security tools offers significant protection. A reliable VPN, whether software-based or a hardware device, encrypts your internet connection, enhancing privacy and security. A comprehensive antivirus and anti-malware suite actively detects and removes malicious software, safeguarding your devices and data. Additionally, a robust password manager generates and securely stores strong, unique passwords, reducing the risk of account breaches.
These essential tools, conveniently available through platforms like Amazon, empower you to browse, shop, and connect online with greater peace of mind. Investing in these solutions is a direct investment in the safety of your personal data, financial well-being, and overall digital life. By encrypting your connection, guarding against malware, and securing your accounts, you create a strong foundation against common online dangers.
Therefore, take control today and build your digital fortress with the right digital security tools. A VPN shields your online activity, antivirus software defends against threats, and a password manager secures your accounts. Embracing these fundamental measures is crucial for navigating the digital world safely and confidently, providing a vital layer of defense in an increasingly interconnected landscape. Prioritize these investments for a more secure digital future.
[LINK SUGGESTION – TYPE: Internal – CONTEXT: Link to a category page for ‘Cybersecurity Guides’ or ‘Software Reviews’ on the site.]
[Closing CTA]
Ready to explore more ways to enhance your online privacy and security? Check out our guide to choosing the best secure browser for your needs.

















